Part 4 of Technology En Masse
Whenever you browse the web, there is always a chance somebody is watching your every move. There is a fair responsibility at developers and website administrators for making surfing safe, such as HTTPS (which we will touch upon in the next post) and encrypting privacy sensitive data. However, in this fourth edition of Technology En Masse we take a look at online security in light of the user; you.
Risks
Finding somebody online
To understand why we are at risk when making use of internet services it is important to have a basic understanding of how the internet works. (If you think you already do, you can skip the next the paragraph.)
Communication over the internet works from computer to computer. Data is sent and received in packages. One such package is comparable to the mail the postman brings. If you request a video from Youtube, Youtube has to send you the video packages over the internet. How do these packages know where to go? Each connection to the internet has a unique address (also called the IP address) and this way Youtube knows exactly where to deliver the package. Your own computer unwraps the package and then you are able to watch the video you requested.
Since the IP address is your location on the internet, it serves as a means of identification. Websites know if you have been there before and can use this identification method to serve you, for instance, with personal recommendations and personalized advertisements. Furthermore since your packages also cross other IP addresses, a gross estimation of your real physical location can be made. Making the IP address not only a means of identification of your digital persona, but also of your physical yourself. Besides for reasons of marketing, this information might be used by governments, the police, but also hackers and thieves.
Man in the middle attack
Considering information flows freely over the internet you can imagine other people noticing it. And thus noticing your requests for certain data. Wrongdoers might abuse this technique in redirecting your package requests to their own computer under water, without you noticing it. This way they can eavesdrop on your connection, or worse; you might enter your password somewhere you didn’t mean to. Hackers can make use of this technique (also known as a Man-in-the-Middle attack) to commit identity theft or steal money from you.
Don’t worry too much however because the chance of this happening to you personally are pretty slim. There is an incredible amount of data going over the internet and picking you (an individual) is really not worth it (when compared to corporate, more valuable, information). Furthermore it is pretty hard to bring this method in practice and only some skilled hackers are able to do so.
Data Logging & Tracking Cookies
In some cases hackers are not your main concern. Websites that you specifically want to make use of can also collect information about you that you are not aware of. They can do this in two ways: tracking you and logging your information. Using your IP address they can track websites you have been visiting before you arrive at their own server (tracking cookies). Larger, more influential, tech companies don’t even need to wait before you decide to contact them, they can track alongside other websites that make use of their services.
A Cookie is a small file that can be kept on your computer specifically linked to a single website. Web developers can use this technique to recognize you and tailor to your needs. For instance if you want a website to ‘remember you‘ so you don’t need to log in every time you visit them again. When you exit a website, this cookie remains on your PC as a kind of deputy to the website. The cookie might however also be recognizable by other websites/services. This way a website can provide information about your visit to (for instance) an advertisement service. You have visited Nike’s website looking for new shoes? Facebook might recognize Nike’s cookie and show you advertorials from Nike’s new edition Jordans. This kind of cookie is often referred to as a tracking cookie. All modern browsers offer the option to disable cookies (be aware you also might loose some helpful aspects of cookies) or you can use plugins for blocking these kind of cookies (e.g. Ghostery).
Tracking cookies are pretty harmless but people dislike them because they are secretly exchanging information about your behavior. More mischievous are data logging utilities applied by big players like Facebook and Google. These websites are so influential and there are so many people using their services that they offer the option to create advance profiles of single users. We have written about this before in Technology En Masse Part 2: Big Data so please read that post if you want a more in-depth explanation. Essentially they are incorporated in so many other websites (as part of their advertisement services) that they can track almost 50% of your online behavior. As a derivative of this behavior they can determine personality traits such as sexual orientation (88 percent accuracy) or affiliation to a specific political party (e.g. Democratic of Republican with 85 percent accuracy).
Solutions
Now after reading about these risks online you might be scared or you might be anxious or you might be not bothered at all. Fact is that there are a couple of (not-too-difficult) steps that one can take to decrease the chance that these methods will be applied on them. There is a certain amount of responsibility at website developers but as a user you should not rely on that. First of we want to state that it all begins with awareness. If you know what to expect you can take appropriate measures. Furthermore you will have to know that getting your personal data 100% safe is an impossible quest. What you are essentially doing is make it more-and-more expensive for someone to get to your data. Lastly you should be aware that in order to gain such privacy there is a reasonable chance you will have to sacrifice a certain level of comfort.
Encrypted browsing
A possible solution to the interception of data either via a man-in-the-middle attack or the logging of data is to make use of encryption. Encryption comes in different forms but in essence it always has to work both ways. The server you are getting your data from has to support the same encryption you have enforced. With encryption you turn the packages that you are about to send over the internet into a suitcase with a lock on it. Such a lock is made for a specific kind of key but if the website you are aiming for uses a different kind of key the suitcase won’t open.
As we have stated before the possibility for encryption is a shared responsibility. Website developers need to offer the right keys to your suitcases. HTTPS is an encryption protocol that is generally used and made available by web developers. You are using a HTTPS connection when you see a lock (green or grey) in the header of your browser. In Technology En Masse Part 5: Certificates and HTTPS we will explain this technique in more detail. The point we want to make right now is that (as a user) you can force the browser to only contact a website when they use this HTTPS protocols. Problem is that you won’t able to reach websites that are not using this protocol.
Virtual Private Network
Virtual private networks (or VPN’s for short) can eliminate this problem to a certain extend. VPN’s offer encrypted connections as an addition to their main service. Up to a certain point your data will be encrypted. This means that enforcing HTTPS is less relevant (however not unimportant!). The main reason to consider a VPN however is to cover up your IP address. As can be seen in the picture a VPN offers a layover before connecting to the website you are aiming for. This way the only address the website sees is the one from your VPN. Websites are not able to link to your physical address or IP address. The main advantage is also you are sharing this one address with multiple users, so data gets scrambled when someone is looking at the requests of all these users.
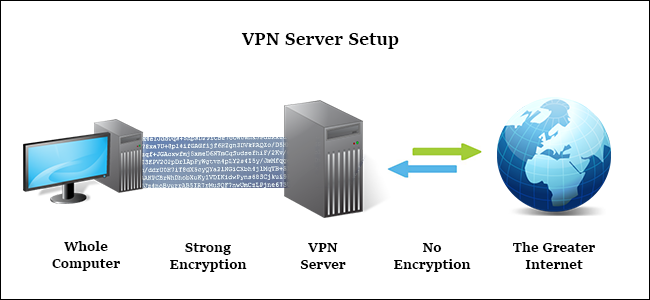 Image from: How To Geek
Image from: How To Geek
Most VPN’s offer an application that you can install on your computer. This application redirects all your internet traffic (so not only your browser, but mail too) via the VPN’s server. Sometimes you can choose what country you want to access the internet from (meaning you make use of a server abroad). VPN services are mostly subscriptions You pay for usage monthly or yearly. When you are picking a VPN subscription, think about two things:
- Pay for the service. If they offer it for free, they are most likely selling your data-usage.
- Consider what they are logging (this is really a trust issue). If your VPN logs every request you make, you are still traceable. Even after months. Read into the workings of the VPN of your liking.
Blocking Browser Extensions
A last, low level, measure you can take as a user is to block unwanted service while you are browsing the web. We mentioned Ghostery for blocking Tracking Cookies. Ghostery is a so called Extension; a micro-application to fit into another application, in this case: your browser. You can install Ghostery by looking under extensions in the browser of your choice. They make use of long lists with advertisement companies and will block advertisement. Furthermore they can detect and block certain tracking options; both from cookies as from other pieces of code implemented by websites (e.g. Facebook). It will not enable you to surf the web in private and you will have to be weary about Ghostery as well. It wouldn’t be the first time a technology like it is bought up by a big player and your connection is still compromised.
Users of online services should not rely on developers to deliver a safe online environment. They are for the main part responsible for their own safety. In this part of Technology En Mass we have described some of the risks you might take going online, because we want to pressure: awareness is the first step into protecting your private information. Furthermore we have mentioned possible measures you can take to decrease the possibilities of exposing your online behavior. You will never be able to reach 100% privacy and untraceability but you can at least decrease a hacker’s chance by making use of VPN’s and encrypted browsing and by blocking tracking cookies. In the next part of Technology En Masse we will dive deeper into what we think are the responsibilities of web developers to ensure the proper use of user-data and encrypted connections.
